OMILIA CONTACT CENTER SECURITY
Multi-layered anti-fraud mechanisms to protect all your self-service channels.

Cyber threats continue to rise, in numbers and sophistication and because of this, utilizing new technologies such as AI, has become crucial for companies to stay ahead of protecting their contact centers and data. The same AI that is improving organizations security, is the same technology that is in the hands of cybercriminals, so staying a step ahead is critical.
Reduce fraud risk and prevent malicious attacks from breaching your contact center with our multi-layered anti-fraud mechanisms and intelligent authentication services.
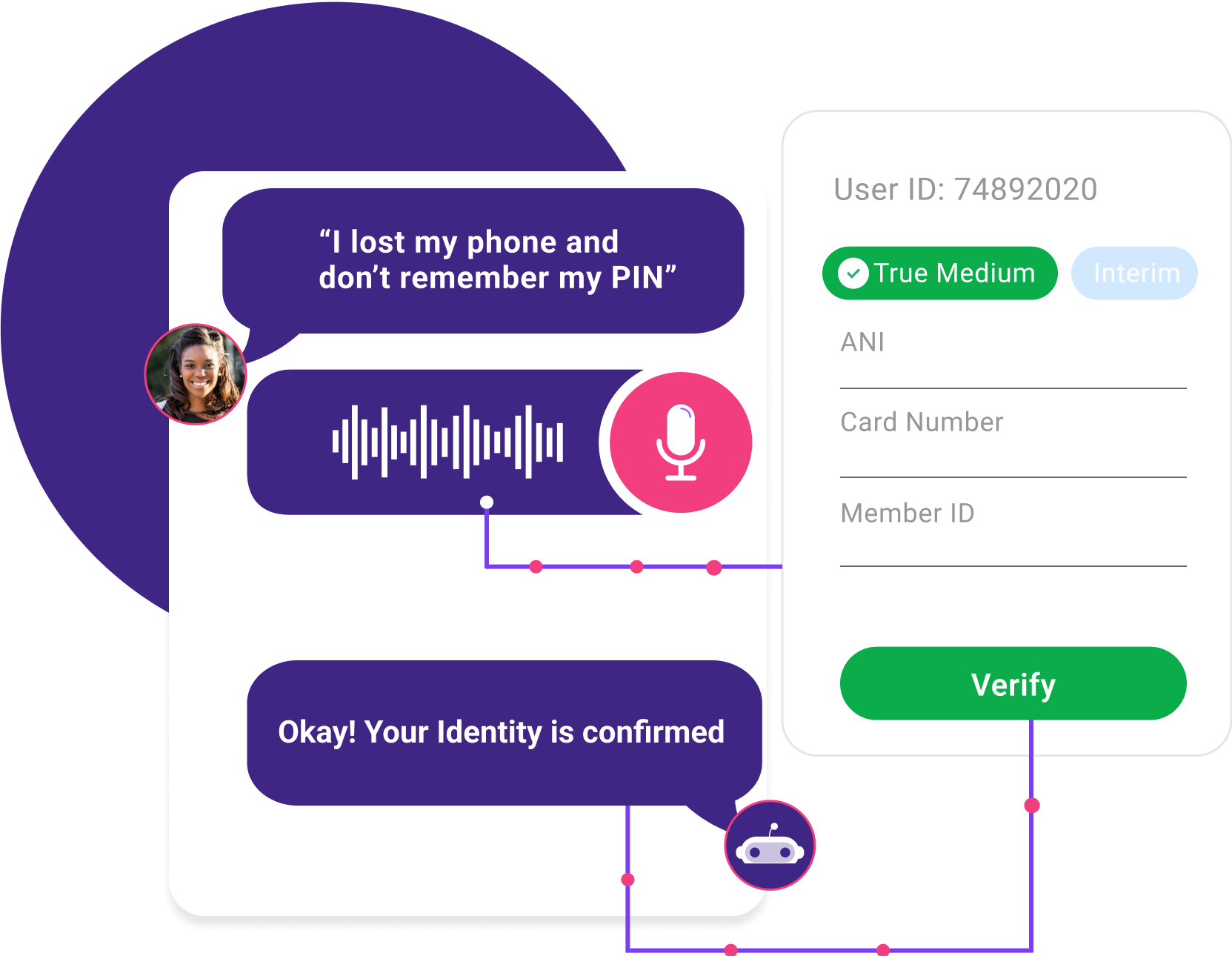
The time is now to invest and implement the appropriate systems that streamline customer authentication to maximize self-service and keep your customers’ data safe.
Voice Biometric Verification
Let customers opt-in to use their voice-based authentication. Enroll callers’ unique biometric voiceprints and then seamlessly verify them the next time they call, with just two seconds of speech, in real-time as they speak to the IVR or human agent.
Liveness Detection
Prevent cases where fraudsters try to attack an account using a synthetic or recorded voice. Every caller’s voice can be thoroughly examined to confirm authenticity, using robust text-to-speech detection algorithms that can dissect synthetic voices. With extreme accuracy it can distinguish between real and artificial voices more accurately than a human listener.
Speaker Change Detection
We identify instances where a different person takes over the phone from the legitimate caller, after the legitimate person successfully authenticates, and escalate the call to an agent or your specialist fraud team.
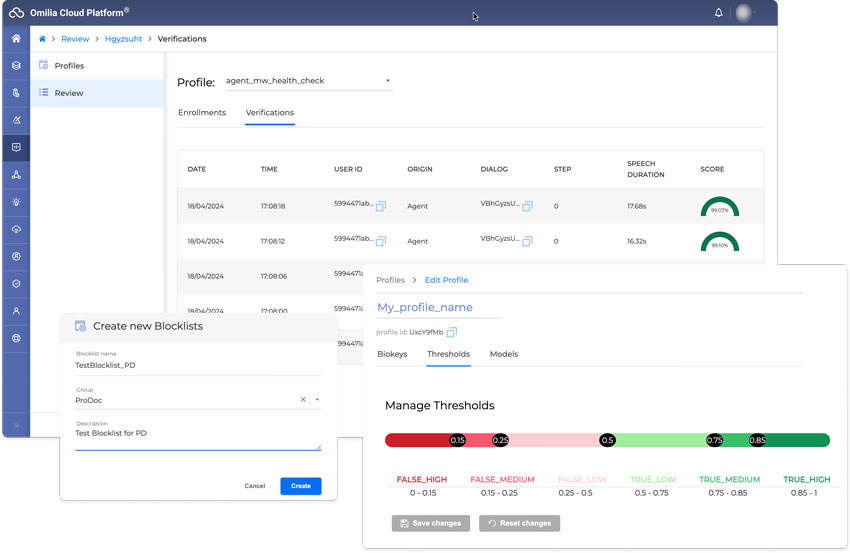
Protect your reputation by identifying and mitigating the risk of fraud, lost revenue and fraud-related penalties. We detect and combat threats to maintain the safety and privacy of your
contact center.
Known Fraudster Blocklisting
Create a database of known fraudulent voices so repeat offenders can be blocked. Calls are checked against the blocklist and virtual or human agents alerted to take the appropriate action.
Behavior Analytics
Behavior analytics help detect unusual actions that signal fraud risk, enabling timely prevention. By analyzing historical data, such as changes in call patterns, suspicious activities can be identified and mitigated to enhance security and improve the user experience.
ANI Spoofing Risk Analysis
Prevent attacks where scammers hide behind a spoofed phone number or try to impersonate someone by using their phone number. Phone numbers are inspected providing a confidence assessment indicating whether the number is legitimate or fraudulent.
01/06/2024
Reviewer Role:
Engineering - Other
Company Size:
10B - 30B USD
Industry:
Banking Industry
Overall, a very positive experience. Vendor is very receptive of their customer feedback. Very good customer service.
Read More24/07/2024
Reviewer Role:
IT Services
Company Size:
10B - 30B USD
Industry:
Banking Industry
Every employee of Omilia I came into contact with is proud of their company and wants every engagement to be a successful one.
Read More05/07/2024
Reviewer Role:
IT
Company Size:
10B - 30B USD
Industry:
Energy and Utilities Industry
Our overall experience with implementing with the Omilia project team was excellent. They quickly understood our requirements and also offered feedback and potential room for improvement.
Read More05/07/2024
Reviewer Role:
IT
Company Size:
10B - 30B USD
Industry:
Energy and Utilities Industry
Collaboration with the project team and their ability to deliver on complex use case requirements such as multi intent transaction automation, alpha-numeric, and multi-language, allowed us to achieve deployment with faster speed to market.
Read More05/07/2024
Reviewer Role:
IT
Company Size:
1B - 3B USD
Industry:
Banking Industry
Stable network that works great for the self-service of our client's needs. Seamless workflow when changes are needed to update intents
Read More11/07/2024
Reviewer Role:
IT
Company Size:
10B - 30B USD
Industry:
Travel and Hospitality Industry
Omilia has gone above and beyond to meet our needs. Our deployment was quick, and the support was excellent.
Read More11/07/2024
Reviewer Role:
IT
Company Size:
10B - 30B USD
Industry:
Travel and Hospitality Industry
We have been very impressed with Omilia's IVR solution and people. Everything from interacting with Omilia staff to requirements gathering and implementation has been exceptional. This IVR was selected due to its AI abilities and so far it has delivered what was promised.
Read More11/07/2024
Reviewer Role:
Engineering - Other
Company Size:
10B - 30B USD
Industry:
Banking Industry
Omilia has been very responsive to issues and questions we have had through the entire process.
Read More15/07/2024
Reviewer Role:
Operations
Company Size:
250M - 500M USD
Industry:
Energy and Utilities Industry
Omilia teams were able to deliver on complex use cases quickly, helping us meet our delivery schedule. They continue to collaborate closely with our teams on IVR optimizations.
Read More15/07/2024
Reviewer Role:
Customer Service and Support
Company Size:
10B - 30B USD
Industry:
Manufacturing Industry
Excellent experience. Leveraged Omilia to deliver an improved customer experience.
Read More16/07/2024
Reviewer Role:
Operations
Company Size:
250M - 500M USD
Industry:
Travel and Hospitality Industry
Omilia has been a great partner from the first POC test to market test.
Read More17/07/2024
Reviewer Role:
Product Management
Company Size:
<50M USD
Industry:
Energy and Utilities Industry
Very responsive and knowledgeable, easy to work with, work ethics are high
Read More18/07/2024
Reviewer Role:
IT
Company Size:
1B - 3B USD
Industry:
Transportation Industry
The implementation team from Omilia was amazing and made our rollout simple. Omilia is a true partner and focuses on how to further our business needs.
Read More18/07/2024
Reviewer Role:
Customer Service and Support
Company Size:
1B - 3B USD
Industry:
Banking Industry
They are always supportive and deliver great service and assistance when needed
Read More19/07/2024
Reviewer Role:
Engineering - Other
Company Size:
250M - 500M USD
Industry:
Banking Industry
Ability to deliver complex use cases with top quality; agility and top speed. Hundreds of out of the box functionalities in the contact center space.
Read More19/07/2024
Reviewer Role:
Product Management
Company Size:
<50M USD
Industry:
Banking Industry
Omilia has been a great partner for us to date, and has been particularly flexible/accomodating to our unique needs. We have a strong POV/vision of vision for IVR both from customer/business and E2E tech stack perspectives, of which Omilia has been fully aligned and supporting.
Read More26/07/2024
Reviewer Role:
Customer Service and Support
Company Size:
500M - 1B USD
Industry:
Energy and Utilities Industry
The team has been very attentive to our needs and expectations and has been fairly consistent with communication. The uptime of the system and updates has been satisfactory.
Read More29/07/2024
Reviewer Role:
Customer Service and Support
Company Size:
500M - 1B USD
Industry:
Banking Industry
This is an exclusive package of functions that is based on the cloud. NLU corresponders perfectly to the Greek Language. The cooperation is at a very high level and efficient and with deliverables as agreed.
Read More29/07/2024
Reviewer Role:
Customer Service and Support
Company Size:
3B - 10B USD
Industry:
Healthcare and Biotech Industry
The Omilia team is compiled of experts. They care about the functionality of their product and the success of their clients. I felt valued as a customer.
Read More29/07/2024
Reviewer Role:
Software Development
Company Size:
3B - 10B USD
Industry:
Banking Industry
Overall, my experience with Omilia has been very good. It's rare to engage with a vendor where it feels like a true partnership, and they care as much about the customer experience as we do.
Read More01/08/2024
Reviewer Role:
Sales and Business Development
Company Size:
250M - 500M USD
Industry:
Telecommunication Industry
Our ICT Sales team resells OCP as part of ICT projects solutions. This is a great experience because: 1) OCP is user-friendly and allows quick deployment, 2) OCP is well accepted from the part of our customers, 3) Omilia is a well committed partner.
Read More05/08/2024
Reviewer Role:
Engineering - Other
Company Size:
30B + USD
Industry:
Banking Industry
Omilia has been an outstanding partner, providing excellent resources to support our growth and system utilization. Their product team aligns with our vision and has delivered numerous enhancements to meet our specific needs.
Read More28/08/2024
Reviewer Role:
IT
Company Size:
10B - 30B USD
Industry:
Energy and Utilities Industry
Omilia has been a great partner. They have delivered amazing AI solutions that fits our needs. The team that has been working with us are phenomenal and best at what they do. They are customer focused and always come up with innovative solutions that are very helpful to our business. Omilia team is very adjustable to the time and needs of the customer.
Read More